Disable This One Apple iPhone Setting to Prevent App Tracking Now - CNET
Updated: 2023-12-31 20:00:04
 The iPhone security boost you didn't know you needed.
The iPhone security boost you didn't know you needed. The iPhone security boost you didn't know you needed.
The iPhone security boost you didn't know you needed. Save $300 on a lifetime subscription to The Fitness App and get expert advice on custom workouts and diet plans to improve your health in the new year.
Save $300 on a lifetime subscription to The Fitness App and get expert advice on custom workouts and diet plans to improve your health in the new year.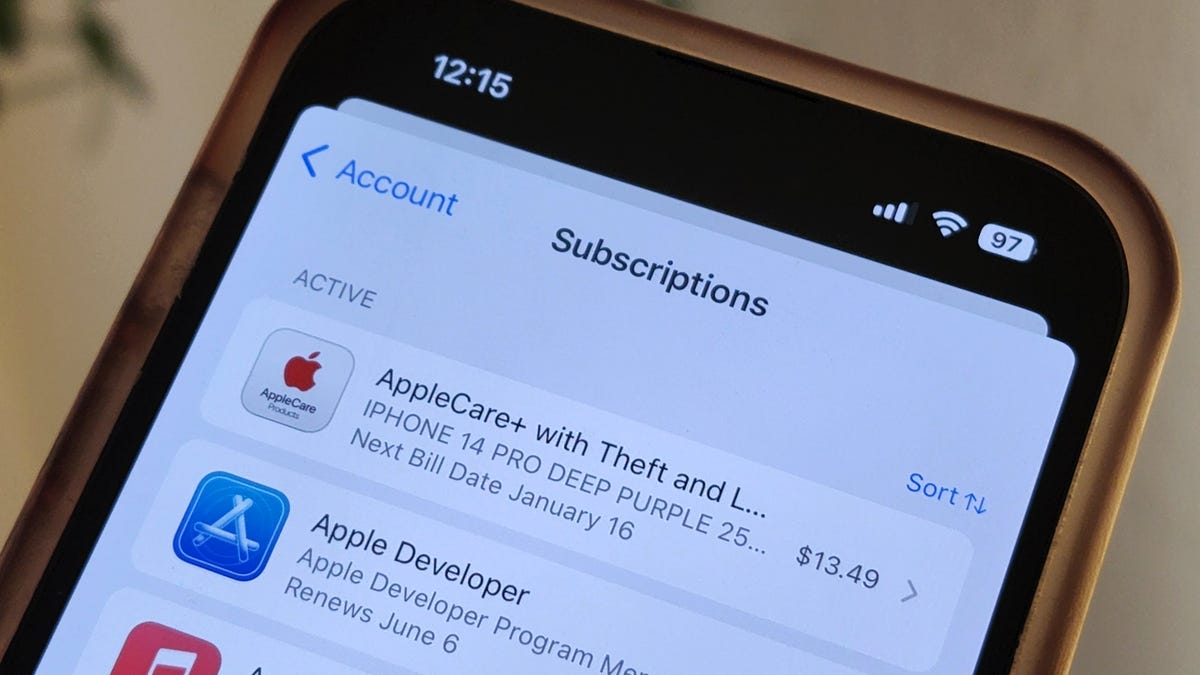 Whether it's a paid service you forgot about or a free trial you never canceled, it's time to end them.
Whether it's a paid service you forgot about or a free trial you never canceled, it's time to end them. Score a full year of Sams' Club membership for just $25 with this limited-time deal.
Score a full year of Sams' Club membership for just $25 with this limited-time deal. You get what you pay for. Free VPNs typically have slower speeds and collect your data.
You get what you pay for. Free VPNs typically have slower speeds and collect your data. X Tech That Died in 2023 Tax Day 2024 Best Phones of 2023 Your Credit Card Debt Go Solar for Cheap Losing Sleep Adds Up Tech Money Home Wellness Home Internet Energy Deals Sleep Price Finder more Tech Services Software Eliminate Annoying iPhone Background Noise With This iOS Feature Your phone calls are about to sound a whole lot better . Zachary McAuliffe Staff writer Zach began writing for CNET in November , 2021 after writing for a broadcast news station in his hometown , Cincinnati , for five years . You can usually find him reading and drinking coffee or watching a TV series with his wife and their . dog Expertise Web hosting , operating systems , applications and software Credentials Apple software beta tester , Helps make our computers and phones work Zach's grandparents See full
X Tech That Died in 2023 Tax Day 2024 Best Phones of 2023 Your Credit Card Debt Go Solar for Cheap Losing Sleep Adds Up Tech Money Home Wellness Home Internet Energy Deals Sleep Price Finder more Tech Services Software Eliminate Annoying iPhone Background Noise With This iOS Feature Your phone calls are about to sound a whole lot better . Zachary McAuliffe Staff writer Zach began writing for CNET in November , 2021 after writing for a broadcast news station in his hometown , Cincinnati , for five years . You can usually find him reading and drinking coffee or watching a TV series with his wife and their . dog Expertise Web hosting , operating systems , applications and software Credentials Apple software beta tester , Helps make our computers and phones work Zach's grandparents See full Head to StackSocial to get lifetime access to the standard plan from Curiosity Stream for $180 and gain access to thousands of documentaries.
Head to StackSocial to get lifetime access to the standard plan from Curiosity Stream for $180 and gain access to thousands of documentaries. Get a new, washable rug for less and transform your home for 2024.
Get a new, washable rug for less and transform your home for 2024. , . X Tech That Died in 2023 Tax Day 2024 Best Phones of 2023 Your Credit Card Debt Go Solar for Cheap Losing Sleep Adds Up Tech Money Home Wellness Home Internet Energy Deals Sleep Price Finder more Why You Can Trust CNET Our expert , award-winning staff selects the products we cover and rigorously researches and tests our top picks . If you buy through our links , we may get a . commission Reviews ethics statement Tech Services Software Amazon Prime Video Will Charge Extra to Remove Ads , Starting Jan . 29 Regular Amazon Prime and Prime Video subscribers will soon have to deal with commercial breaks , unless they pay an additional fee . Imad Khan Senior Reporter Imad is a senior reporter covering Google and internet culture . Hailing from Texas , Imad started his journalism career in
, . X Tech That Died in 2023 Tax Day 2024 Best Phones of 2023 Your Credit Card Debt Go Solar for Cheap Losing Sleep Adds Up Tech Money Home Wellness Home Internet Energy Deals Sleep Price Finder more Why You Can Trust CNET Our expert , award-winning staff selects the products we cover and rigorously researches and tests our top picks . If you buy through our links , we may get a . commission Reviews ethics statement Tech Services Software Amazon Prime Video Will Charge Extra to Remove Ads , Starting Jan . 29 Regular Amazon Prime and Prime Video subscribers will soon have to deal with commercial breaks , unless they pay an additional fee . Imad Khan Senior Reporter Imad is a senior reporter covering Google and internet culture . Hailing from Texas , Imad started his journalism career in X Tech That Died in 2023 Tax Day 2024 Best Phones of 2023 Your Credit Card Debt Go Solar for Cheap Losing Sleep Adds Up Tech Money Home Wellness Home Internet Energy Deals Sleep Price Finder more News Privacy Google Settles 5 Billion Consumer Privacy Suit Over Chrome's Incognito Mode The company is accused of secretly tracking Chrome users while they were in the incognito browsing mode . Imad Khan Senior Reporter Imad is a senior reporter covering Google and internet culture . Hailing from Texas , Imad started his journalism career in 2013 and has amassed bylines with The New York Times , The Washington Post , ESPN , Tom's Guide and Wired , among . others Expertise Google , Internet Culture See full bio Imad Khan Dec . 29, 2023 1:05 p.m . PT The lawsuit , potentially covering millions of
X Tech That Died in 2023 Tax Day 2024 Best Phones of 2023 Your Credit Card Debt Go Solar for Cheap Losing Sleep Adds Up Tech Money Home Wellness Home Internet Energy Deals Sleep Price Finder more News Privacy Google Settles 5 Billion Consumer Privacy Suit Over Chrome's Incognito Mode The company is accused of secretly tracking Chrome users while they were in the incognito browsing mode . Imad Khan Senior Reporter Imad is a senior reporter covering Google and internet culture . Hailing from Texas , Imad started his journalism career in 2013 and has amassed bylines with The New York Times , The Washington Post , ESPN , Tom's Guide and Wired , among . others Expertise Google , Internet Culture See full bio Imad Khan Dec . 29, 2023 1:05 p.m . PT The lawsuit , potentially covering millions of X Apple Halts Sale of Watches Tech That Died in 2023 Tax Day 2024 Best Phones of 2023 Your Credit Card Debt Go Solar for Cheap Losing Sleep Adds Up Tech Money Home Wellness Home Internet Energy Deals Sleep Price Finder more Tech Mobile New iPhone 15 or iPhone 15 Pro Change These 4 iOS 17 Settings Right Now If you got a brand new iPhone for Christmas , here's how to better customize your experience . Nelson Aguilar Nelson Aguilar is an LA-based tech how-to writer and graduate of UCLA . With more than a decade of experience , he covers Apple and Google and writes on iPhone and Android features , privacy and security settings and . more See full bio Nelson Aguilar Dec . 27, 2023 4:05 a.m . PT 3 min read Your iPhone 15 Pro comes with iOS 17. James Martin CNET Christmas is now over , and if
X Apple Halts Sale of Watches Tech That Died in 2023 Tax Day 2024 Best Phones of 2023 Your Credit Card Debt Go Solar for Cheap Losing Sleep Adds Up Tech Money Home Wellness Home Internet Energy Deals Sleep Price Finder more Tech Mobile New iPhone 15 or iPhone 15 Pro Change These 4 iOS 17 Settings Right Now If you got a brand new iPhone for Christmas , here's how to better customize your experience . Nelson Aguilar Nelson Aguilar is an LA-based tech how-to writer and graduate of UCLA . With more than a decade of experience , he covers Apple and Google and writes on iPhone and Android features , privacy and security settings and . more See full bio Nelson Aguilar Dec . 27, 2023 4:05 a.m . PT 3 min read Your iPhone 15 Pro comes with iOS 17. James Martin CNET Christmas is now over , and if Tech Money Home Wellness Energy Home Internet Deals Reviews New Price Finder More Close Join Login Tech Home Entertainment Mobile Computing Services Software Gaming Money Credit Cards Mortgages Insurance Loans Cryptocurrency Banking Investing Taxes Home Home Internet Home Security Kitchen Household Smart Home Energy Utilities Yard Outdoors Wellness Sleep Nutrition Fitness Personal Care Parenting Medical Mental Health News Culture Politics Social Media Privacy Misinformation Culture Internet Culture Entertainment Sports Videos Science Climate Space Biology Deals Reviews Reviews Best Products Versus Gift Guide Shopping Extension Cars Best Cars Car Accessories Car Reviews Car News Car Prices Coupons Vistaprint Coupons StubHub Discount Codes H M Coupons ExpressVPN Coupons Home Depot Coupons
Tech Money Home Wellness Energy Home Internet Deals Reviews New Price Finder More Close Join Login Tech Home Entertainment Mobile Computing Services Software Gaming Money Credit Cards Mortgages Insurance Loans Cryptocurrency Banking Investing Taxes Home Home Internet Home Security Kitchen Household Smart Home Energy Utilities Yard Outdoors Wellness Sleep Nutrition Fitness Personal Care Parenting Medical Mental Health News Culture Politics Social Media Privacy Misinformation Culture Internet Culture Entertainment Sports Videos Science Climate Space Biology Deals Reviews Reviews Best Products Versus Gift Guide Shopping Extension Cars Best Cars Car Accessories Car Reviews Car News Car Prices Coupons Vistaprint Coupons StubHub Discount Codes H M Coupons ExpressVPN Coupons Home Depot Coupons X Last-Minute Gifts on Amazon Tech That Died in 2023 Tax Day 2024 Best Phones of 2023 Your Credit Card Debt HDR TV Formats Explained Losing Sleep Adds Up Tech Money Home Wellness Home Internet Energy Deals Sleep Price Finder more Why You Can Trust CNET Our expert , award-winning staff selects the products we cover and rigorously researches and tests our top picks . If you buy through our links , we may get a . commission Reviews ethics statement Home Home Security Need a Cheap Home Security Camera Try an Old iPhone or Android Smartphone You don't have to recycle or donate that old mobile phone unless you really want to Megan Wollerton Former Senior Writer Editor See full bio Megan Wollerton Dec . 25, 2023 8:30 a.m . PT 4 min read iPhone and Android apps make it simple to turn an old phone
X Last-Minute Gifts on Amazon Tech That Died in 2023 Tax Day 2024 Best Phones of 2023 Your Credit Card Debt HDR TV Formats Explained Losing Sleep Adds Up Tech Money Home Wellness Home Internet Energy Deals Sleep Price Finder more Why You Can Trust CNET Our expert , award-winning staff selects the products we cover and rigorously researches and tests our top picks . If you buy through our links , we may get a . commission Reviews ethics statement Home Home Security Need a Cheap Home Security Camera Try an Old iPhone or Android Smartphone You don't have to recycle or donate that old mobile phone unless you really want to Megan Wollerton Former Senior Writer Editor See full bio Megan Wollerton Dec . 25, 2023 8:30 a.m . PT 4 min read iPhone and Android apps make it simple to turn an old phone X Last-Minute Gifts on Amazon Tech That Died in 2023 Tax Day 2024 Best Phones of 2023 Your Credit Card Debt HDR TV Formats Explained Losing Sleep Adds Up Tech Money Home Wellness Home Internet Energy Deals Sleep Price Finder more Tech Mobile You Can Fix the Most Annoying iOS 17 Features on Your iPhone You're not going to love everything about iOS 17 and that's OK . Nelson Aguilar Nelson Aguilar is an LA-based tech how-to writer and graduate of UCLA . With more than a decade of experience , he covers Apple and Google and writes on iPhone and Android features , privacy and security settings and . more See full bio Nelson Aguilar Dec . 25, 2023 5:15 a.m . PT 3 min read iOS 17 is great , but you might not love every . feature James Martin CNET iOS 17 brings several new major features to the
X Last-Minute Gifts on Amazon Tech That Died in 2023 Tax Day 2024 Best Phones of 2023 Your Credit Card Debt HDR TV Formats Explained Losing Sleep Adds Up Tech Money Home Wellness Home Internet Energy Deals Sleep Price Finder more Tech Mobile You Can Fix the Most Annoying iOS 17 Features on Your iPhone You're not going to love everything about iOS 17 and that's OK . Nelson Aguilar Nelson Aguilar is an LA-based tech how-to writer and graduate of UCLA . With more than a decade of experience , he covers Apple and Google and writes on iPhone and Android features , privacy and security settings and . more See full bio Nelson Aguilar Dec . 25, 2023 5:15 a.m . PT 3 min read iOS 17 is great , but you might not love every . feature James Martin CNET iOS 17 brings several new major features to the X Last-Minute Gifts on Amazon Tech That Died in 2023 Tax Day 2024 Best Phones of 2023 Your Credit Card Debt HDR TV Formats Explained Losing Sleep Adds Up Tech Money Home Wellness Home Internet Energy Deals Sleep Price Finder more Tech Services Software Stop Deleting Photos on Your iPhone to Free Up Storage and Do This Instead If you keep getting the dreaded message that your iPhone's storage is low , check out these settings before you start deleting pictures , videos and apps . Nelson Aguilar Nelson Aguilar is an LA-based tech how-to writer and graduate of UCLA . With more than a decade of experience , he covers Apple and Google and writes on iPhone and Android features , privacy and security settings and . more See full bio Nelson Aguilar Dec . 24, 2023 7:00 a.m . PT 4 min read NurPhoto
X Last-Minute Gifts on Amazon Tech That Died in 2023 Tax Day 2024 Best Phones of 2023 Your Credit Card Debt HDR TV Formats Explained Losing Sleep Adds Up Tech Money Home Wellness Home Internet Energy Deals Sleep Price Finder more Tech Services Software Stop Deleting Photos on Your iPhone to Free Up Storage and Do This Instead If you keep getting the dreaded message that your iPhone's storage is low , check out these settings before you start deleting pictures , videos and apps . Nelson Aguilar Nelson Aguilar is an LA-based tech how-to writer and graduate of UCLA . With more than a decade of experience , he covers Apple and Google and writes on iPhone and Android features , privacy and security settings and . more See full bio Nelson Aguilar Dec . 24, 2023 7:00 a.m . PT 4 min read NurPhoto Grab yourself a smart lock with this end-of-year sale at Wellbots and save $80.
Grab yourself a smart lock with this end-of-year sale at Wellbots and save $80. : tells you what's new and why it . matters To help you navigate a world of accelerating , change so you are empowered to make decisions about what to do or buy . next Who We Are Mission Our Story Our Experts What We Do Our Reach Contact Us We guide you to a better future . We believe you can create a better future when you understand new ideas . Our experts give you news , tools and advice that help you navigate our ever-changing world . Because when you understand whatâ s going on , you can do something about it . We're here to help everyone become the heroes of their own . stories Lindsey Turrentine , EVP , Content and Audience , CNET Read Lindsey's Welcome Letter We anticipate what's next and act first . All About Computers CNET goes on-air to give audiences knowledge on all things .
: tells you what's new and why it . matters To help you navigate a world of accelerating , change so you are empowered to make decisions about what to do or buy . next Who We Are Mission Our Story Our Experts What We Do Our Reach Contact Us We guide you to a better future . We believe you can create a better future when you understand new ideas . Our experts give you news , tools and advice that help you navigate our ever-changing world . Because when you understand whatâ s going on , you can do something about it . We're here to help everyone become the heroes of their own . stories Lindsey Turrentine , EVP , Content and Audience , CNET Read Lindsey's Welcome Letter We anticipate what's next and act first . All About Computers CNET goes on-air to give audiences knowledge on all things . , Product Security for everyone 1Password Personal Personal For you and your . family 1Password Business Business For growing . businesses 1Password Enterprise Enterprise For security at . scale 1Password Developer Tools Developer Keep secrets out of . code View 1Password features Whatâ s New Unlock with SSO to secure every login Unlock 1Password with Okta , Azure , Duo , OneLogin , JumpCloud , and . more Save and sign in with passkeys Go passwordless today and start using passkeys with 1Password in the browser and 1Password for . iOS Customize policies for a secure fit Create , manage , and enforce policies to govern how and where employees use . 1Password View plans Talk to sales Download 1Password Resources Explore Learn Security Security How 1Password is . different Resource Library
, Product Security for everyone 1Password Personal Personal For you and your . family 1Password Business Business For growing . businesses 1Password Enterprise Enterprise For security at . scale 1Password Developer Tools Developer Keep secrets out of . code View 1Password features Whatâ s New Unlock with SSO to secure every login Unlock 1Password with Okta , Azure , Duo , OneLogin , JumpCloud , and . more Save and sign in with passkeys Go passwordless today and start using passkeys with 1Password in the browser and 1Password for . iOS Customize policies for a secure fit Create , manage , and enforce policies to govern how and where employees use . 1Password View plans Talk to sales Download 1Password Resources Explore Learn Security Security How 1Password is . different Resource Library